What is a Trojan horse
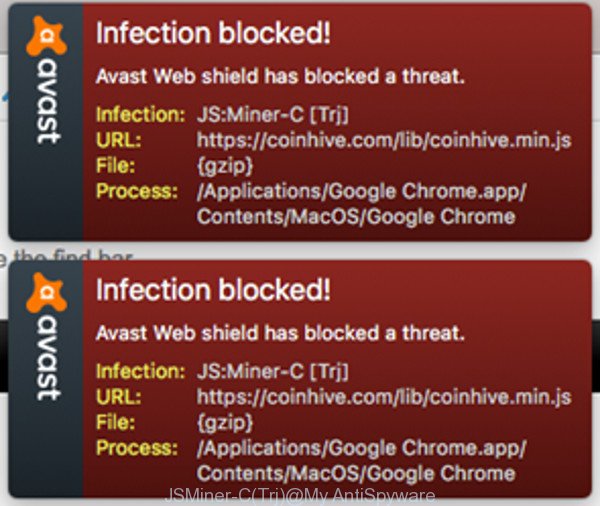
Hello, I've contracted JS:Miner-C on my MacBook Air, and can't seem to remove it. Can anyone help with the removal of this from my Mac? I've Avast installed, but this only seems to detect it and doesn't remove the trojan. Miner inside of image file. How to find out if your browser is secretly mining, and what you can do about it. Avast antivirus products detect these embedded miners. In addition, there are a few other strategies you can employ to see if your browser is mining: Check to see what scripts your browser has loaded.
A Trojan Horse is a type of malware that pretends to be something useful, helpful, or fun while actually causing harm or stealing data. Trojans are often silently downloading other malware (e.g. spyware, adware, ransomware) on an infected device as well. One of the most dangerous Trojans is Zeus.
View and Download GE MAC 5000 operator's manual online. Resting ecg analysis system. MAC 5000 Medical Equipment pdf manual download. Medical Equipment GE MAC 2000 Operator's Manual. Ecg analysis system (226 pages). Select Fax machine to transmit to facsimile machine. Use IR for Select Yes to enable the local infrared serial line. MAC™2000ECGAnalysisSystem Operator'sManual SoftwareVersion1.1 2053535-002RevisionC. Manual Biocompatibility. 2053535-002C MAC™2000ECGAnalysisSystem 25. Introduction SerialNumberFormat(cont'd.) Item Name Description. View and Download GE MAC 2000 operator's manual online. ECG Analysis System. MAC 2000 Medical Equipment pdf manual download. GE Mac 2000 ECG Machine, 12-lead Resting ECG System $ 3,495.00 $ 2,935.00 The New MAC 2000 Resting ECG System with the Marquette. 12SL. analysis program can help to avoid variations in care delivery by standardizing ECG information from the physician office through the hospital. Mac 2000 ecg machine manual. Ge healthcare. Read online or download PDF. GE Healthcare MAC 2000 User Manual.
Where a Trojan comes from
Trojan viruses often are spread via an infected email attachment or a download that hides in free games, applications, movies or greeting cards.
How to recognize a Trojan virus
Your computer will often slow down because of the burden on the processor. The best way to identify if you have been infected is to use a Trojan scanner, found in any Trojan removal software.
How to remove a Trojan virus
It's best to use a trojan remover that can detect and remove any Trojans on your device. Manual removal of whenvideoup mac. The best, free Trojan remover is included in Avast Free Antivirus. When removing Trojans manually, be sure to remove any programs from your computer that are affiliated with the Trojan.
How to prevent Trojan viruses
- Avoid opening unknown files attached to email. These have extensions such as .exe, .vbs, and .bat.
- Maintain up-to-date antivirus protection, preferrably with a firewall.
Yesterday I ran a full system scan using my Avast antivirus software and it found a infection file. The file's location is :
Avast categorizes the infection file as :
So, after deleting the file I did several more full system scans to check to see if there were any more files. I found nothing, until I restarted my macbook pro today. The file reappeared in the same location. So I decided to let Avast put it in the virus chest, restarted the laptop, and again the file was in the same location again. Therefore the virus is re-creating the file every restart of the laptop.
I want to avoid wiping the laptop and re-installing everything, so that is why I am here. I researched the file path and cryptonight and found out that cryptonight is/can be malicious code that can run in the background of someone's computer to mine cryptocurrency. I've been monitoring my CPU usage, Memory, and Network and I haven't seen a single odd process running. My CPU is running below 30%, my RAM is generally below 5GB (installed 16GB), and my network hasn't had any processes sending out/receiving large amount of data. So if something is mining in the background, I can't tell at all. I have no clue what to do.
My Avast runs full system scans every week, so this just recently became an issue this week. I checked all of my chrome extensions and nothing is out of order, I haven't downloaded anything special within the past week, besides the new Mac operating system (macOS High Sierra 10.13.1). So I have no clue where this has came from to be honest and I have no clue how to get rid of it. Can someone please help me out.
I suspect that this supposed “virus” is coming from the Apple update and that it is just a pre-installed file that is created and runs every time the OS is booted/rebooted. But I am unsure since I only have one MacBook and no one else that I know that has a mac has updated the OS to High Sierra. But Avast keeps labeling this as a potential “Cryptonight” virus and no one else online has posted anything about this issue. Therefore, a common virus removal forum isn't helpful in my situation, since I've already attempted to remove it with both Avast, malwarebytes, and manually.
JakeGould1 Answer
Pretty sure there is no virus, malware or trojan at play and his is all a highly coincidental false positive.
It’s most likely a false positive since /var/db/uuidtext/ is related to the new “Unified Logging” subsystem that was introduced in macOS Sierra (10.2). As this article explains:
The first file path (/var/db/diagnostics/) contains the log files. These files are named with a timestamp filename following the pattern logdata.Persistent.YYYYMMDDTHHMMSS.tracev3. These files are binary files that we’ll have to use a new utility on macOS to parse them. This directory contains some other files as well including additional log *.tracev3 files and others that contain logging metadata. The second file path (/var/db/uuidtext/) contains files that are references in the main *.tracev3 log files.
Back Buttons. The Canon 5D Mark IV has a number of buttons on the back of the camera that also serve particular needs. To the top right of the camera, you can find three buttons: AF-ON, AE Lock (Asterisk) and AF Area Mode. When Autofocus Fails MF: Manual Focus Set the lens’s focus mode switch to MF. Will be displayed on the LCD panel. Focus on the subject. Focusing ring Focus by turning the lens focusing ring until the subject looks sharp in the viewfinder. Mar 29, 2019 The AF Point layout for the Canon 5D Mark IV. The Canon 5D Mark IV has 61 selectable AF points distributed through the central portion of the viewfinder. These are the tiny squares that you see in your viewfinder. The system is designed. Canon offers a wide range of compatible supplies and accessories that can enhance your user experience with you EOS 5D Mark IV that you can purchase direct. Scroll down to easily select items to add to your shopping cart for a faster, easier checkout. How to manual focus canon 5d mark iv to mac.
But in your case the “magic” seems to come from the hash:
Just check out this reference for known Windows malware files that references that one specific hash. Congratulations! Your Mac has magically created a filename that matches a known vector that has been primarily seen on Windows systems… But you are on a Mac and this filename is just a hash that is connected to the “Unified Logging” database system’s file structure and it is completely coincidental that it matches that malware filename and should not mean anything.
Manual backup mac to external hard drive. Windows 7 windows 8black, silver, grey, white hard drive, portable hard drive, metal edition, titanium, blue, red, my book duo, metallic silver, thunderbolt, Western Digital, Toshiba. In El Capitan OSX - How to install and use a Seagate backup plus, Slim, Central,fast, 200gb 300gb 400gb 500gb 1tb, 2tb, 3tb, 4tb, 5tb, 6tb 7tb 8tb 9b 10tb 20tb, 40gb 50gb 60gb 70gb 80gb 90gb. Usb 3.0, usb 2.0, usb 4.0 journaled or exfat? Fat 32?Macbook Pro, iMac, macbook air, laptop mac, desktop, computer apple, macbook retina display, macbook air, mac mini, mac pro, Yosemite OS X, Mavericks OS X, tiger OS X.
And the reason that specific file seems to regenerate is based on this detail from the above explanation:
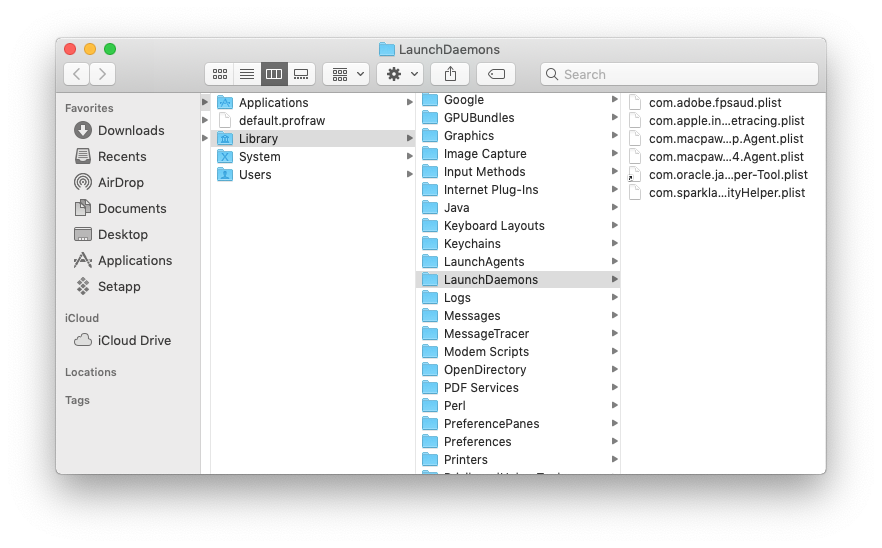
The second file path (/var/db/uuidtext/) contains files that are references in the main *.tracev3 log files.
So you delete the file in /var/db/uuidtext/, but all it is is a reference to what is in /var/db/diagnostics/. So when you reboot, it sees it is missing and recreates it in /var/db/uuidtext/.
As for what to do now? Well, you can either tolerate the Avast alerts or you can download a cache cleaning tool such as Onyx and just force the logs to be recreated by truly purging them from your system; not just that one BC8EE8D09234D99DD8B85A99E46C64 file. Hopefully the hash names of the files it regenerates after a full cleaning won’t accidentally match a known malware file again.
UPDATE 1: It seems like Avast staff acknowledges the issue in this post on their forums:
I can confirm this is a false positive. The superuser.com post describes the issue quite well - MacOS seems to have accidentally created a file that contains fragments of malicious cryptocurrency miner which also happen to trigger one of our detections. Mac awp050 specs.
Now what is really odd about this statement is the phrase, “…MacOS seems to have accidentally created a file that contains fragments of malicious cryptocurrency miner.”
What? Is this implying that someone on the core macOS software development team at Apple somehow “accidentally” setup the system so it generates neutered fragments of a known malicious cryptocurrency miner? Has anyone contacted Apple directly about this? This all seems a bit crazy.
UPDATE 2: This issue is further explained by someone Radek Brich the Avast forums as simply Avast self-identifying itself:
Hello, I'll just add a bit more information.
The file is created by MacOS system, it's actually part of 'cpu usage' diagnostic report. The report is created because Avast uses the CPU heavily during the scan.
The UUID (7BBC8EE8-D092-34D9-9DD8-B85A99E46C64) identifies a library which is a part of Avast detections DB (algo.so). The content of the file is debugging information extracted from the library. Unfortunately, this seems to contain a string which is in return detected by Avast as a malware.
(The 'rude' texts are probably just names of malware.)
JakeGouldJakeGouldprotected by Community♦Nov 26 '17 at 20:07
Avast Js Miner Mac Manual ' 1
Mac Manual Download
Thank you for your interest in this question. Because it has attracted low-quality or spam answers that had to be removed, posting an answer now requires 10 reputation on this site (the association bonus does not count).
Would you like to answer one of these unanswered questions instead?